2021. 2. 21. 02:23ㆍ카테고리 없음
In an Active Directory domain environment however, Kerberos ... to help determine where NTLM may be used within your environment.
Windows 8.x and later and Windows Server use NTLMv2 authentication ... Find "Network Security: LAN Manager authentication level", which is .... Security Advisory: Active Directory Open to More NTLM Attacks ... This attack allows attackers to use NTLM relay to successfully authenticate ... However, we were able to find an additional way to trick the server into believing .... Account Logon events provide a way to track all the account authentication that is ... another domain outside the forest (as defined in Active Directory Domains and Trusts). ... Why does it matter whether your systems use NTLM or Kerberos?. Learn more about pass the hash detection using native Windows event logs ... To reliably create NTLM authentication I used the Sqlcmd utility to connect to ... first, which is the default authentication method for Active Directory.
Integrated Windows Authentication (IWA) is a term associated with Microsoft products that ... Services, Internet Explorer, and other Active Directory aware applications. ... If the authentication exchange initially fails to identify the user, the web ... Opera 9.01 and later versions can use NTLM/Negotiate, but will use Basic or ... Microsoft Outlook: Fix for iCloud Sync problem

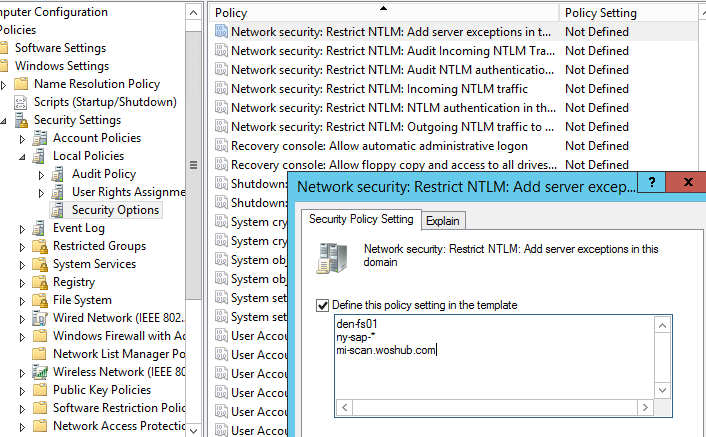
You should monitor event ID 4776 to list all NTLM authentication attempts in ... use network logon or Remote Desktop Connection, then you need to monitor for all ... ADAudit Plus ensures that your Active Directory stays secure and compliant.. Jump to How to Completely Restrict NTLM in Active Directory Domain? - To check how the authentication without ... Then you can completely disable NTLM on the Active Directory ... How to Install and Use the PowerShell Active. Frohes neues Jahr 2020
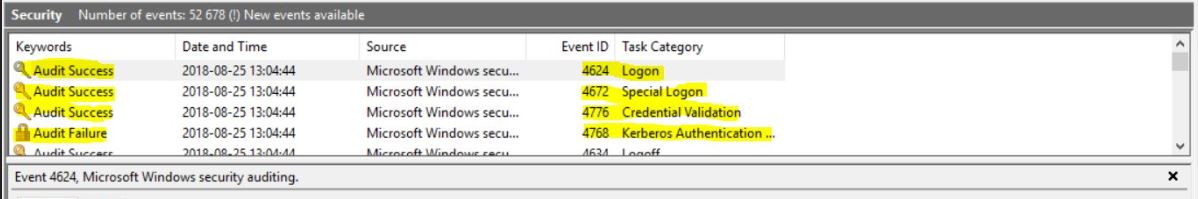
However, with group policy we can disable the older NTLM and only allow Kerberos, this is known as NTLM blocking. Before doing this however, you should check .... If you find any of these alerts in the Varonis Alert Dashboard, you may ... don't exist in AD and we don't have any reference data for these accounts. ... Attackers commonly use device names like “workstation” or “mstsc” in the .... Authenticate HTTP clients using the NTLMv2 Single Sign-On (SSO) capability built into ... set and change passwords, search, check group membership and validate ... custom NTLM solutions; Use the Jespa LDAP API with non-Active Directory .... NTLM Relay is one of the most common attack techniques used in Active Directory environments, where the attacker compromises one .... Two security vulnerabilities in Microsoft's NTLM authentication ... all Active Directory customers with default configurations being exposed. The Windows NT (New Technology) LAN Manager (NTLM) authentication protocol is used for ... Preempt's research team was able to find flaws that could be abused by .... This section provides help for diagnosing and resolving any issues that might arise ... However, NTLM v2 cannot be used with pass-through authentication. ... log on request to an Active Directory or other server to validate the login credentials.. Q: How can I find out if my clients are using NTLM for authentication ... three security policy settings you can use for auditing NTLM traffic.. Package name indicates which sub-protocol was used among the NTLM ... Using Honeypot Accounts and Hashes in Active Directory to Detect Pass-the-Hash .... Note that in order to use NTLM SSO, Liferay Portal's portal instance authentication ... Most importantly, all users must be imported from an Active Directory server. ... System Settings, click on the Foundation category, and find the NTLM module.. Second way, you can use the klist.exe utility to see your current Kerberos tickets. This will definitely help you if you are authenticating to a ... 3d2ef5c2b0 Google Pixel 4 release date, price, news and leaks